Identity & Access Management OTAC
We enable organizations to manage digital identities and control user access to critical corporate information.
Pain points
The business environment is changing rapidly, causing many companies to modify their work environment and procedures. With remote work and the use of personal mobile devices as access cards, obtaining and sharing information has become easier than ever. At the same time, however, the open network environment opens up businesses to significant risks in privacy protection.
- RF cards at risk of loss, theft, and duplication
A total of 90% of the access control market is dominated by RF cards that communicate on frequency. However, because of the risk of duplication and loss, its security is questionable. The card’s security needs to be bolstered to avoid duplication or usage when lost or stolen. Recently, the replacement of smartphones with a simple mobile ID (App) is also gaining attention.
- ID/PW theft because of weak remote work /network separation environment
Because of the COVID-19 crisis, remote workers became susceptible to the negative effects of social engineering methods. In particular, 91.5% of related cyber threats are from email phishing. A separate security control means access to the internal network of the company is the most important aspect of remote work. The use of a VPN to provide end-to-end encryption is recommended. However, using a VPN without a secondary authentication can expose the authentication to theft.
- Information centralized to smartphones
Personal ID and payments are now all available on smartphones. As a result, people rely more and more on their mobile devices. If a person is unable to use a smartphone to access facilities such as public offices, military bases, power plants, etc. that have a commanding security environment, which prevents photography, transmission of information, etc., other IDs and tools for access control will be required.
Solutions
SSenStone’s OTAC provides control to users in mobile and remote work environments or grants a certain level of authority to access corporate resources and networks. It also offers more efficient control by providing a safe and simple authentication process when physical access to a certain space is required. OTAC can be provided both as software and hardware to upgrade individual or corporate access management.
- Provide unidirectional code generated by the client without communication with the server
- Generate a dynamic code that changes every time and is safe from hacking and leakage
- Block attacks in advance with one-time code that does not allow cloning and spoofing attacks
- Protect devices by issuing a unique code that never overlaps with other connected devices
OTAC for Identity and Access Management
OTAC is a revolutionary authentication technology enabling enterprises to secure and protect data and people. Users can generate dynamic one-time access codes from their own mobile devices in an off-the-network environment with which users have access to corporate resources and networks. OTAC can also be easily integrated with the existing IAM solution and the user experience is never compromised.
Device <> Device Authentication
-
Existing
-
OTAC
AI 스피커 로그인 및 결제
매번 변경되는 센스톤의 일회성 인증 코드를 본인의 고유 음성으로 읽는 것만으로 AI 스피커를 활성화시킬 수 있습니다. 진공 청소기, TV, 냉장고, 쇼핑 등 IoT 기기와의 페어링부터 결제까지 안전한 인증을 바탕 으로 AI 스피커 기술과 생태계를 확장할 수 있습니다.
.png)
OTAC는 통신 네트워크가 없는 상황에서도 IFF가 고유한 다이내믹 코드를 생성하고, 생성값을 인증하여, 단방향으로 간편하게 타깃을 식별할 수 있도록 하는 혁신적인 인증 기술입니다. OTAC 기술을 활용하여 생성된 단방향 다이내믹 코드는 아군 식별 및 적의 신호 도용 방지에 적용됩니다.
User <> Service / Device Authentication
-
Existing
-
OTAC
AI 스피커 로그인 및 결제
매번 변경되는 센스톤의 일회성 인증 코드를 본인의 고유 음성으로 읽는 것만으로 AI 스피커를 활성화시킬 수 있습니다. 진공 청소기, TV, 냉장고, 쇼핑 등 IoT 기기와의 페어링부터 결제까지 안전한 인증을 바탕 으로 AI 스피커 기술과 생태계를 확장할 수 있습니다.
.png)
OTAC는 통신 네트워크가 없는 상황에서도 IFF가 고유한 다이내믹 코드를 생성하고, 생성값을 인증하여, 단방향으로 간편하게 타깃을 식별할 수 있도록 하는 혁신적인 인증 기술입니다. OTAC 기술을 활용하여 생성된 단방향 다이내믹 코드는 아군 식별 및 적의 신호 도용 방지에 적용됩니다.
OTAC for integrated management including access/payment/ID
Enterprises issue and manage at least 3.5 cards per each employee for payment, identification, and access purposes such as employee ID cards, corporate credit/debit cards, and corporate OTP for online payment, and this may not be fun. To spare themselves the hassles from going through all necessary steps, people tend to rely on their mobiles more for integrated functions, which, unfortunately, raises other issues such as excessive reliance on a single device resulting in quick battery draining. Further, restrictions on use in certain areas such as government offices, military bases, power plants, and closed network environments could be an issue too. With OTAC embedded-IC Chip (dual interface chip, NFC supported) card and minimal use of smartphones or access devices, however, many of the above-mentioned issues can be solved. You may enjoy diverse functions with the card including payment, access management, system login, and identity authentication.
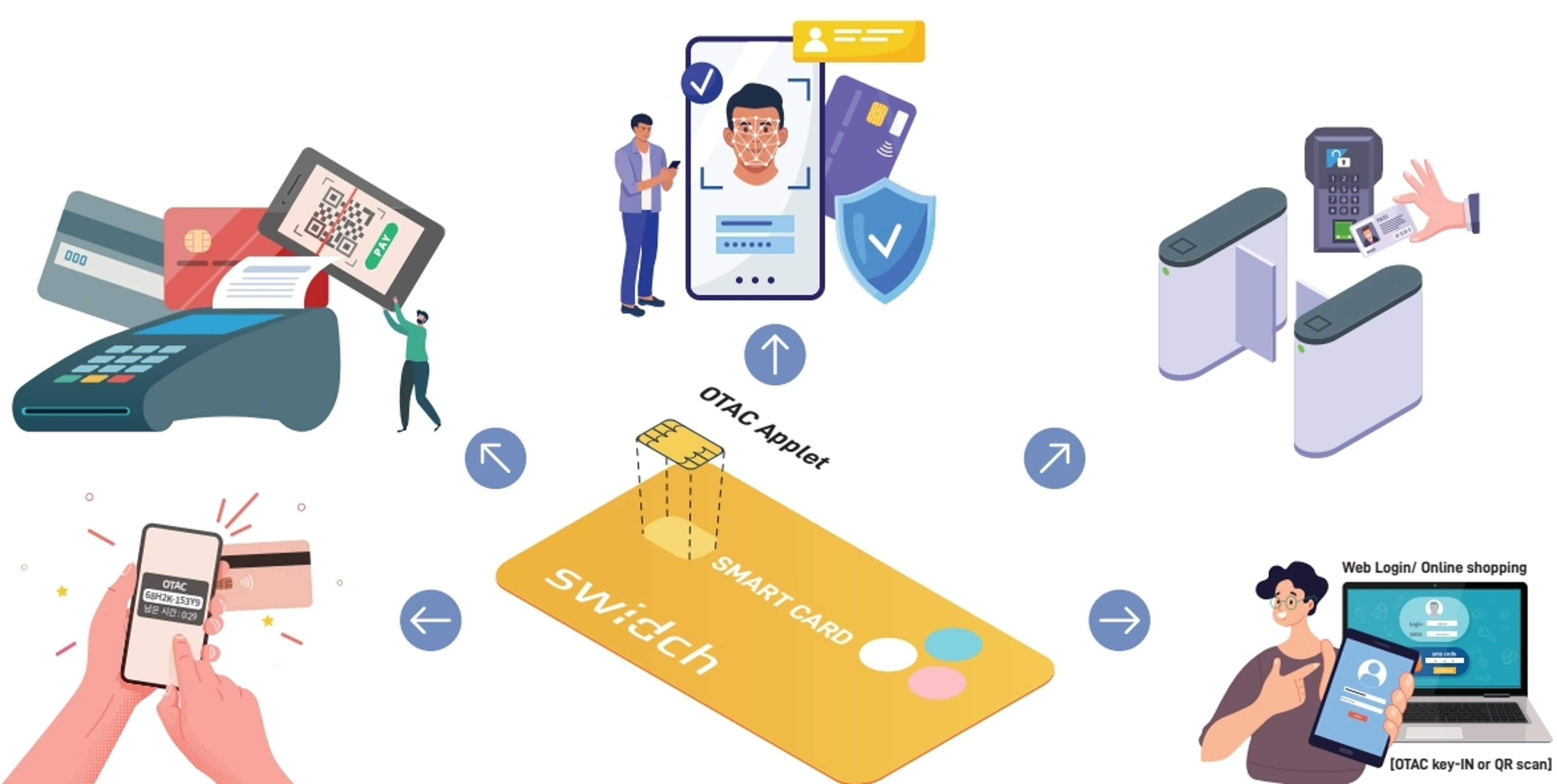
OTAC Access Management Product

OTAC Applet IC Card
- IC Card type : Combi Card (ISO 7816)
- OTAC Code generation through NFC card tapping (mobile phone and access gate)
- Various functions from gate/door access to system login and OTP functions
- Expandable to payment cards through a partnership with financial service firms
- Fingerprint sensor and display option available

Fingerprint OTAC Card
- Using energy-harvesting technology (No Battery)
- OTAC Code generation through fingerprint recognition
- OATC code or QR code generation (for access control)
- Can utilize a non-network environment
- E-ink Display option available (QR Code applicable)
- System log in and gate/door access control all available

OTAC Mobile App
- OTAC log in code generation through card tapping, bio-authentication on mobile device, etc.
- Using fingerprint recognition or ID card
- Using mobile-generated code or QR code
- Can utilize non-network environment
- Additional function can be linked (App functions)
-System log in and gate/door access control all available
OTAC Access Management Service
Web/App Login
A user’s ID and password are a typical fixed-value authentication method, and even the most complex passwords can easily be hacked. Multi-factor authentication (MFA), PIN and password, biometrics, etc. have been proposed to address this issue, but a simpler and more efficient
authentication technology is required as the number of complex access environments and processes continue to rise. OTAC logs its users
using mobile app–based biometrics, and its security is bolstered by single-use dynamic codes that never recur.
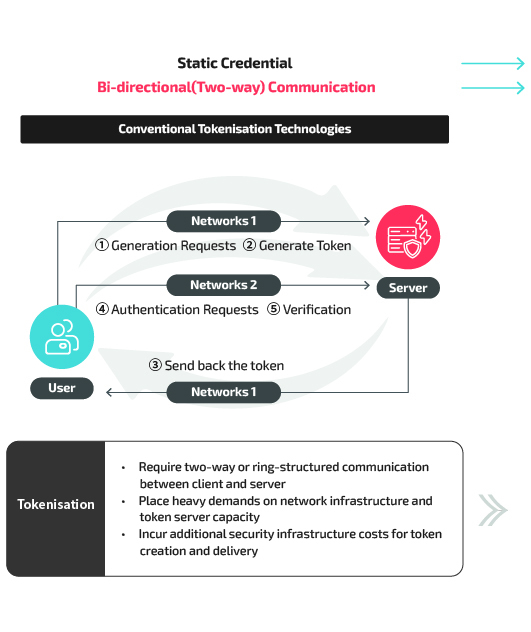
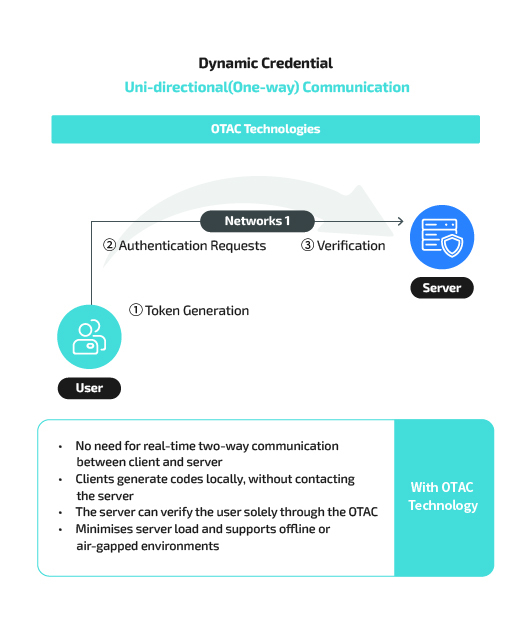
Physical Access Control
The security hole of radio-frequency identification (RFID) cards is as a result of using static key values. If stolen, all other cards can become
exposed. Access control cards using OTAC, on the other hand, generate dynamic codes in regular intervals through a mobile app, allowing
safer access control by copying these in a near-field communication (NFC) card. Dynamic codes used in authentication are only available for a
certain period, preventing their misuse when duplicated or lost.
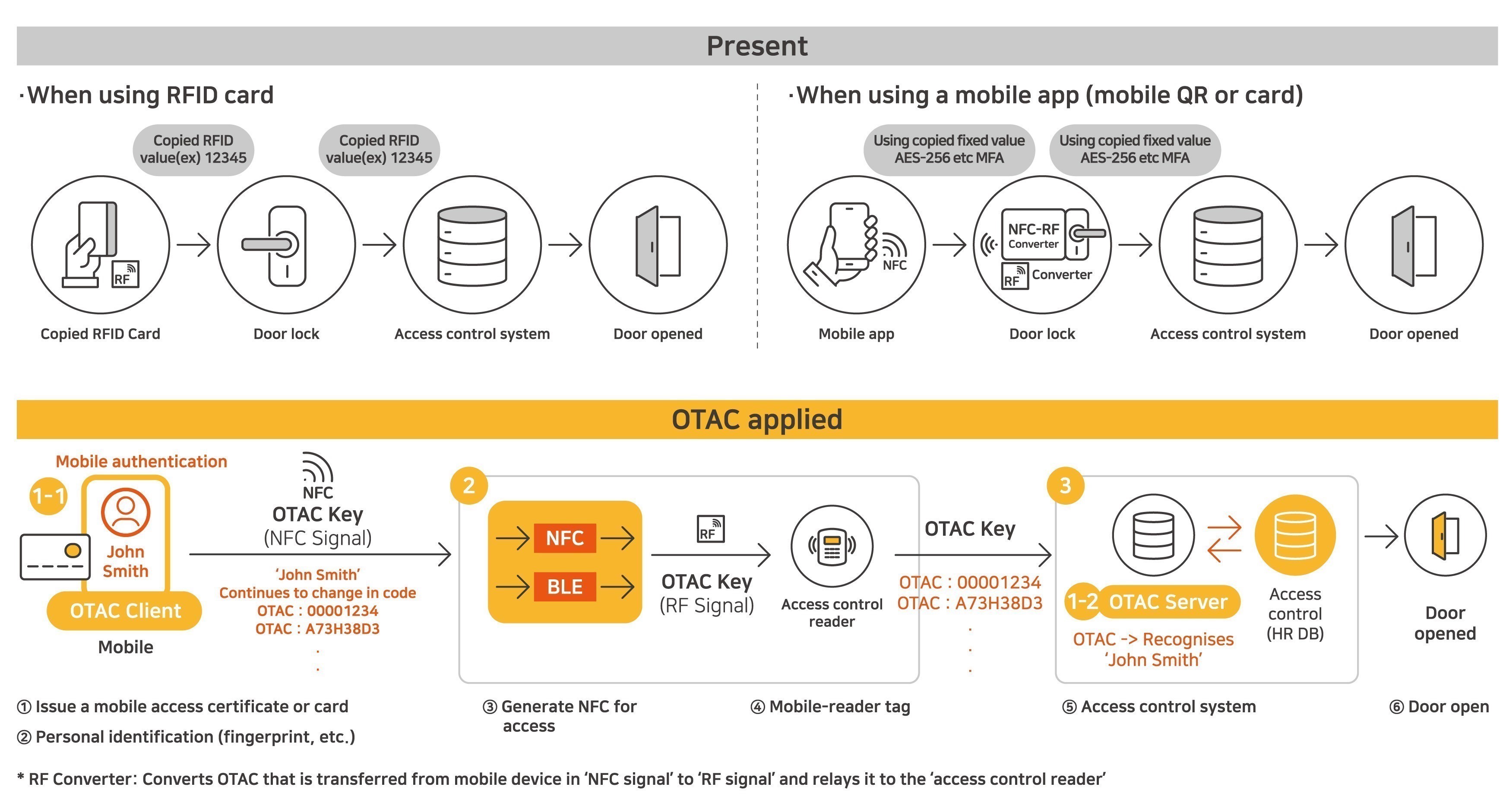
OTAC for enterprise
With OTAC, users can generate dynamic one-time access codes from their own mobile devices. This works in an off-the-network environment. As a result, enterprises can reduce network traffic and enable secure, reliable access management as there is no surface for hackers to attack.
Furthermore, employees and their devices can be identified with the code alone. Therefore, employees no longer have to deal with certain IDs, passwords and tokens. Also, there is no need to force employees to change their password regularly because OTAC itself is a dynamic code that changes every time!
Why OTAC
OTAC, developed by SSenStone, is the original technology that provides all of the following features at the same time.
-
OTAC is a dynamic code, which means the code keeps changing. As a result, you don’t need to worry about any leak of your personal information, such as your card details, because the codes must have already been changed when others try to use them.
-
The network connection is NOT necessary at all for generating OTAC.
Reducing an authentication stage that requires the network connection directly means there are fewer gateways for the hackers to access our personal information.
Moreover, this feature enables users to authenticate even when they are in networkless environments, such as on the plane, underground, rural or foreign areas. -
swIDch can guarantee that the code never duplicates with anyone at any given moment.
There is NO chance of someone else having the same code. -
The users or their devices can be identified with the code alone.
Once OTAC has been generated, providing OTAC alone is already fully sufficient to identify the user as the code is unique.
It means, you can forget about the bundles of static information including IDs and passwords.
OTAC Algorithm Analysis and Academic Verification

New Excellent Technology (NET) Certification Acquired

SSenStone has received the NET Certification from the Ministry of Trade, Industry, and Energy for its "Individual IoT Device Authentication and Transmission Data Security Technology through Unidirectional Dynamic Authentication (OTAC)."
International Common Criteria (CC) Certification Achieved
.png?width=150&height=150&name=%EA%B5%AD%EC%A0%9CCC%EC%9D%B8%EC%A6%9D_%EC%97%A0%EB%B8%94%EB%9F%BC%20(png).png)
OTACTokenV1.0, the authentication solution based on the world’s first unidirectional dynamic authentication technology, OTAC, has earned the international Common Criteria (CC) certification. For more information, please refer to the press release.
OTAC for Phygital Wins IR52 Jang Yeong-sil Award

SSenStone's OTAC for Phygital has been awarded the 40th-week IR52 Jang Yeong-sil Award for 2024, hosted by the Ministry of Science and ICT. For more details, please visit the official IR52 Jang Yeong-sil Award homepage or the press release.
Insights
Contact Us
make your service reliable with SSenStone!
Inquire now.
5F, 329, Cheonho-daero Dongdaemun-gu, Seoul, Republic of Korea
Contact below if you have an urgent inquiry.
Korea Office (SSenStone)
5F, 329, Cheonho-daero Dongdaemun-gu, Seoul, Republic of Korea (02622)
Tel : 02-569-9668 | Fax : 02-6455-9668
im@ssenstone.com
UK Office (swIDch)
Floor 1, 3 More London SE1 2RE, United Kingdom
Tel : 020-3283-4563
info@swidch.com

.svg)
.svg)
.svg)
.svg)