Drone OTAC
Revolutionize Drone security, safety and regulatory requirements with our patented OTAC technology.
Pain points
The Drone industry is rapidly developing and impacting our daily lives in numerous and innovative ways. It has the ability to change our lives for the better in ways that are hard to comprehend. However, with this innovation comes the potential negative impact of security breaches and exploitation from external rogue sources. SSenStone’s patented technology enhances drone security solutions to keep the device and product in secured modes at the same time, with simple use cases for many different purposes.

- Security : Hijacking
Drones, hacked or hijacked its secured data by various threats, not only pose economic problems but also create serious issues surrounding the safety of individuals and national defense. Drone attacks such as the 2019 drone attack on KSA’s biggest petrochemical facility complex, run by ARAMCO, the Saudi Oil Company, by YEMEN’s rebel forces, or the unidentified Drone incident at Gatwick Airport, London in 2018 which resulted in the cancellation of over 1,000 flights and a 36-hour stand-off serve as a stark reminder at the potential negative impact drone misuse can pose. These cases are close to our days from our lives and are not only bound to national regulation, but to the need to enhance the security and control system of Drone solutions to prevent these potential threats.
Drone communications with remote controllers are often encrypted. However, the encrypted codes are often the same (i.e. static), which makes it a good and easy target for hijacking. For drones, having a lightweight solution both on a physical and digital level is essential. This relates directly to the power consumption and its battery life. In military drones, extra hardware, CMVP (Cryptographic Module Validation Program) is installed to drones to validate the security level in communications. You can imagine why this is necessary for the military. Commercial drones on the other hand are usually relatively light and small, meaning extra hardware installation is a big burden. Therefore, small commercial drones often rely on the existing encrypted communication methods which are relatively easy to hijack.
- Safety : Identification
When drones are mis-used, safety is always the biggest concern. Drones are small, fast, and relatively difficult to detect in comparison to a flying jet. It is an important issue when multiple aircraft, both manned and unmanned, are flying, each device needs to identify and communicate with each other to guarantee safety and a successful mission. This is precisely the reason why there is a need for an identification system for drones and their operators. The economic cost of an unidentified drone near an airport is 500,000 euros for every 30 mins an airport is stopped from operating.
- Regulation : Compliance issues
Aviation authorities such as the Federal Aviation Administration (FAA) in the U.S have started to introduce a number of new regulations as more people own drones, and also to give guidelines on how to operate drones in a safe and useful manner.
One of the key regulations to take effect very soon is Remote ID. This is a new regulation introduced by the FAA and it is the “ability of a drone in flight to provide identification and location information that can be received by other parties”, such as law enforcement. To comply with this upcoming regulation, drone manufacturers are having to implement a solution to embed identification capabilities on the drone in accordance with the standards given by the FAA. The drone pilots/operators must also register themselves with the FAA before they can legally fly the drones.
Solutions
SSenStone upgrades Drone solutions by preventing the use of static information and providing single-channeled dynamic codes to eliminate external threats. OTAC technology, which can be applied to both the software and hardware, maintains and enhances the robust security environment level required for Drone manufacturers and system operators.
OTAC Drone Command
Once the pilot securely accesses the control system via OTAC Pilot ID, the pilot can have full confidence in the security level of the command communication to the drone. Thanks to SSenStone command, every single command generated from the remote controller will be in a ‘one-time, dynamic’ form. This means that every single command is unique, and even if a hacker obtains the command information, the command will be different next time around, meaning it prevents attacks like replay attacks and many more eliminating any risk of drone hijacking.
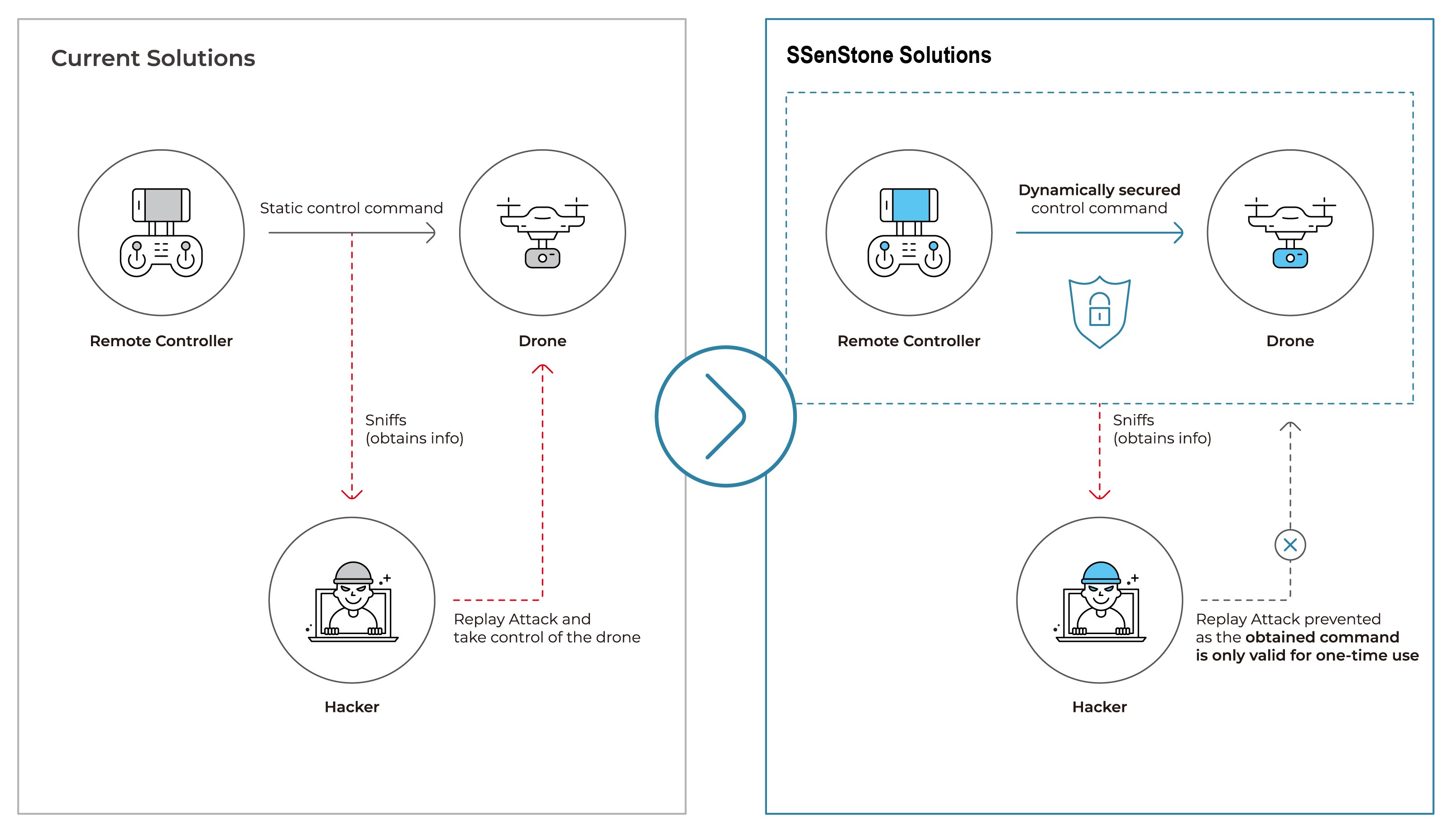
OTAC Drone Authentication
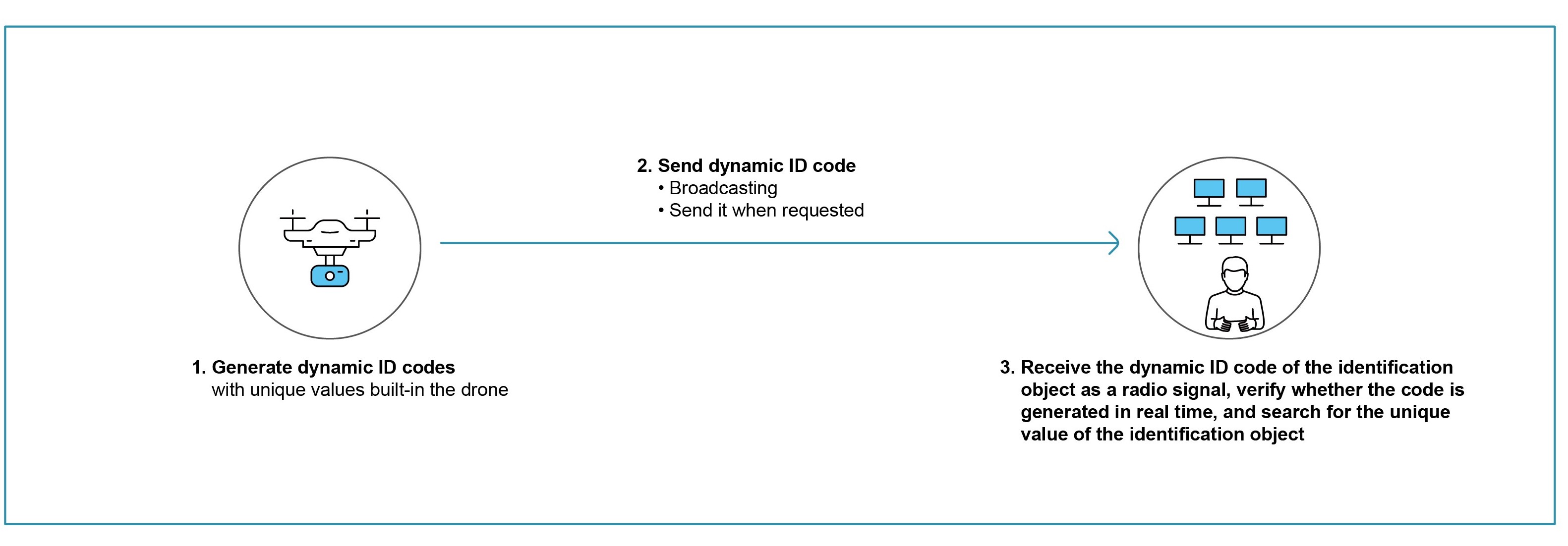
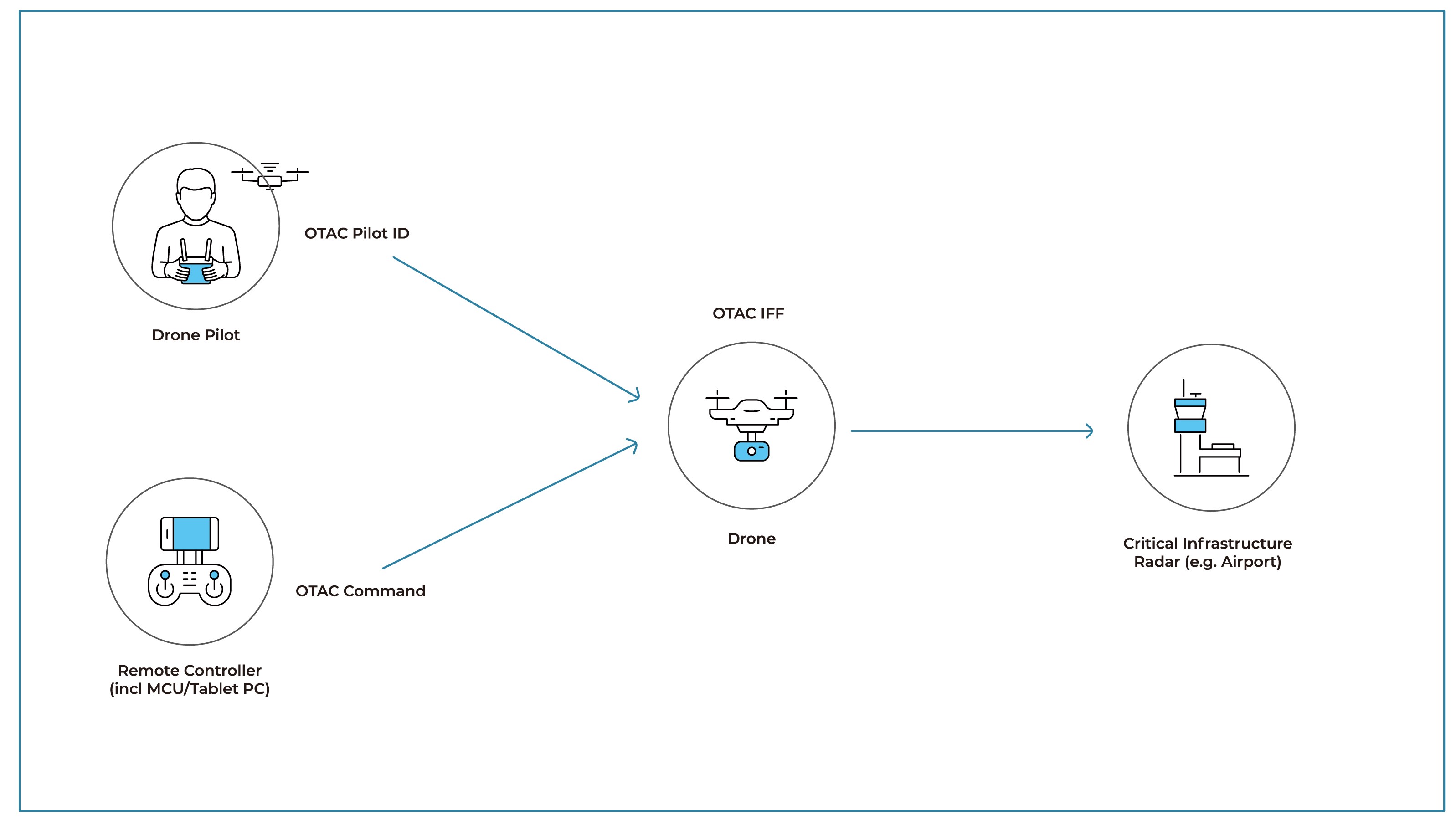
OTAC IFF(Identification of Friendly or Foe)
Identification friend or foe (IFF) is an identification system designed for command and control. It sends an encrypted signal to determine
whether it is a friend or a foe by the return signal, but commands can be stolen and misused. OTAC, a real-time dynamic ID code generated in the off-the-network environment, can identify friends whilst preventing theft and misuse of ID codes by the enemy.
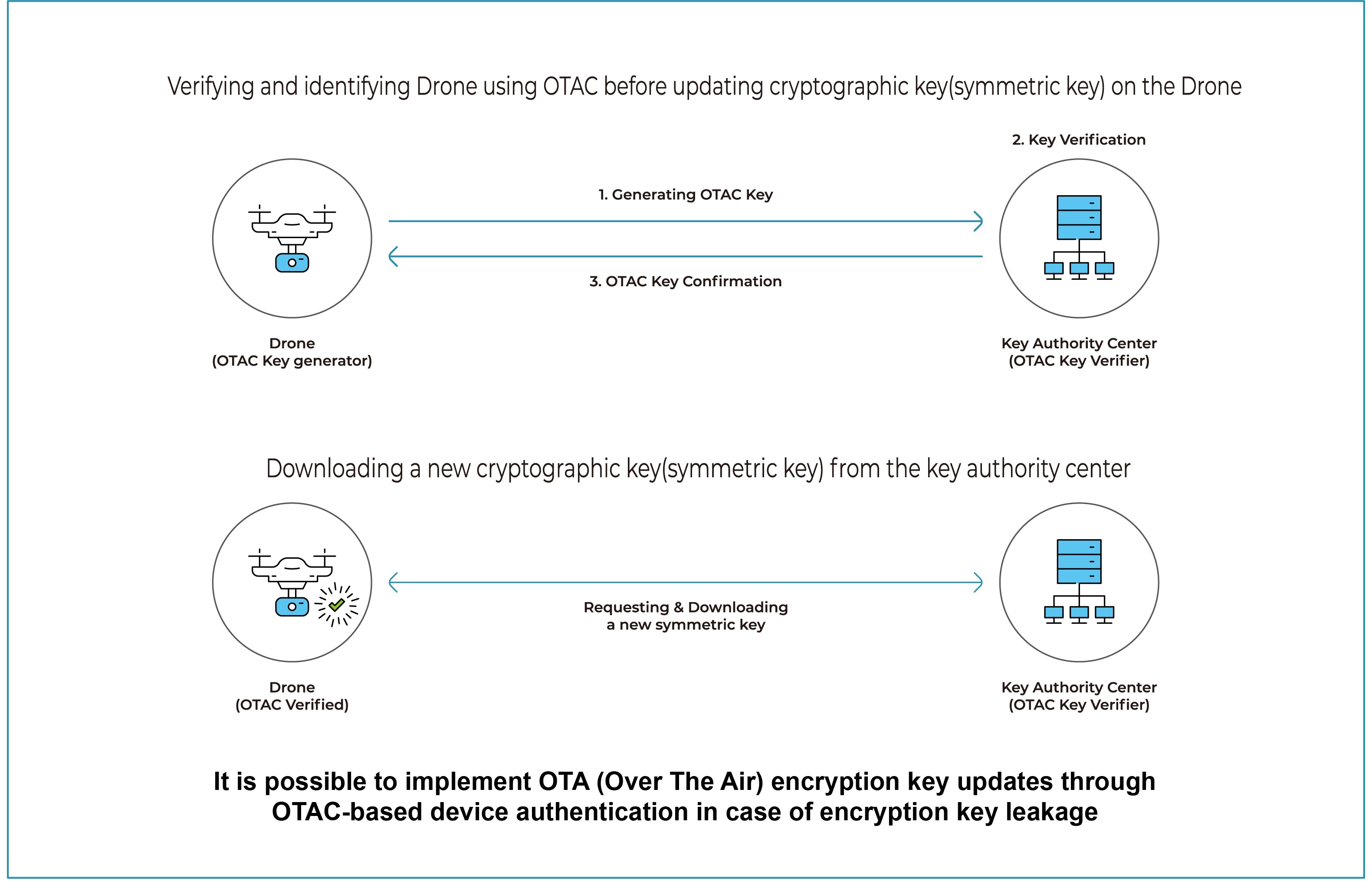
OTAC Authentication for CMVP(Cryptographic Module Validation Program)
OTAC can be used to protect communication encryption modules that have received CMVP certification and to authenticate key-value updates. It provides an improved security environment by using dynamic codes for the identification and verification process of the drone accessed to download the new keys.
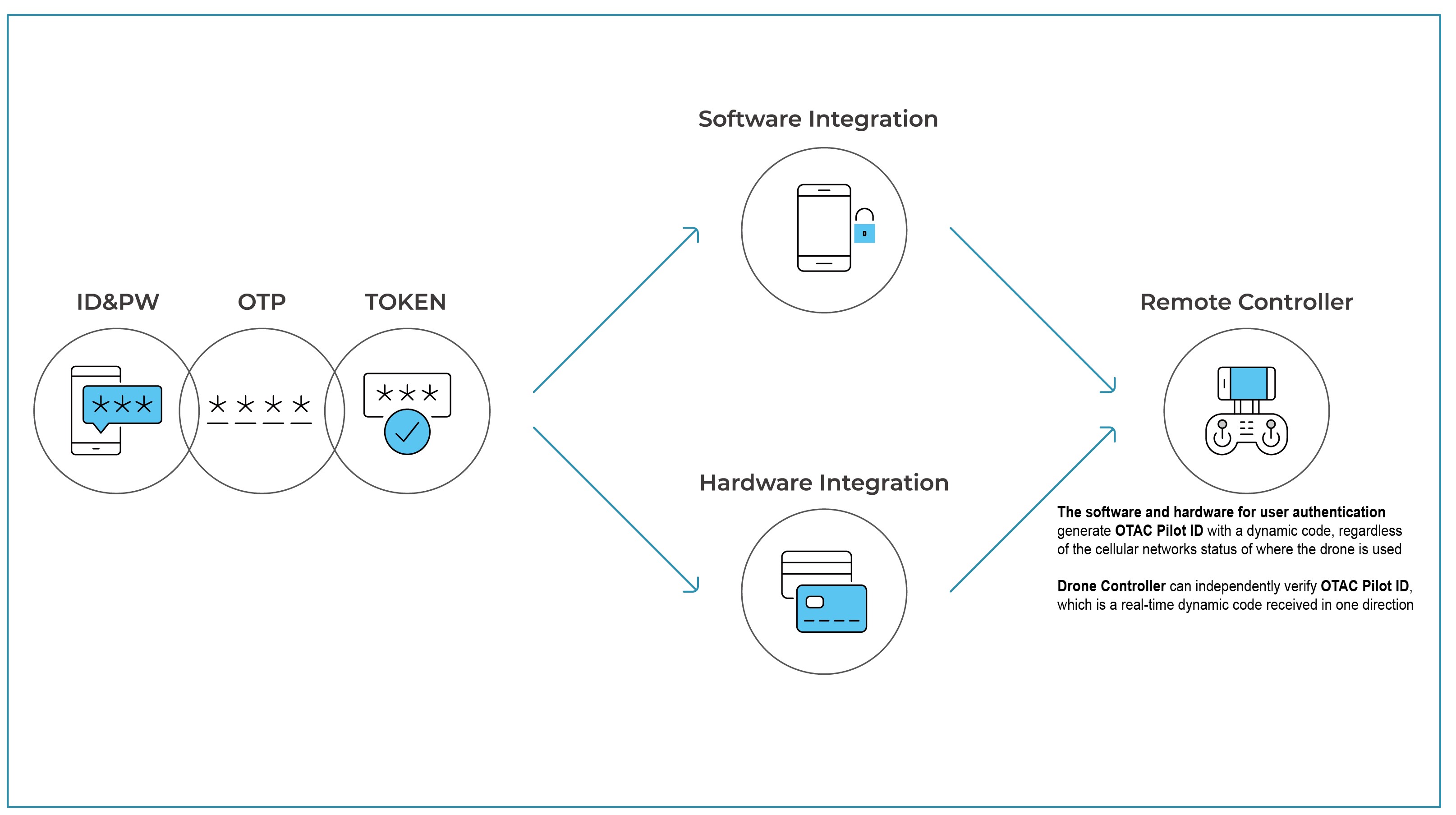
OTAC Pilot Access Management
OTAC Pilot ID
OTAC ensures that licensed pilots are provided with the highest level of security when accessing drone remote systems. Pilots can use SSenStone's mobile app or display card to authenticate themselves and securely access drone control systems.
OTAC Pilot ID&IFF
OTAC converts all commands among the pilot, the controller, and the drone into a one-time dynamic code to enable safe communication. If there is a security issue with the pilot, controller, or drone, you can immediately re-evaluate the status of the drone and register it as an enemy drone and take actions.
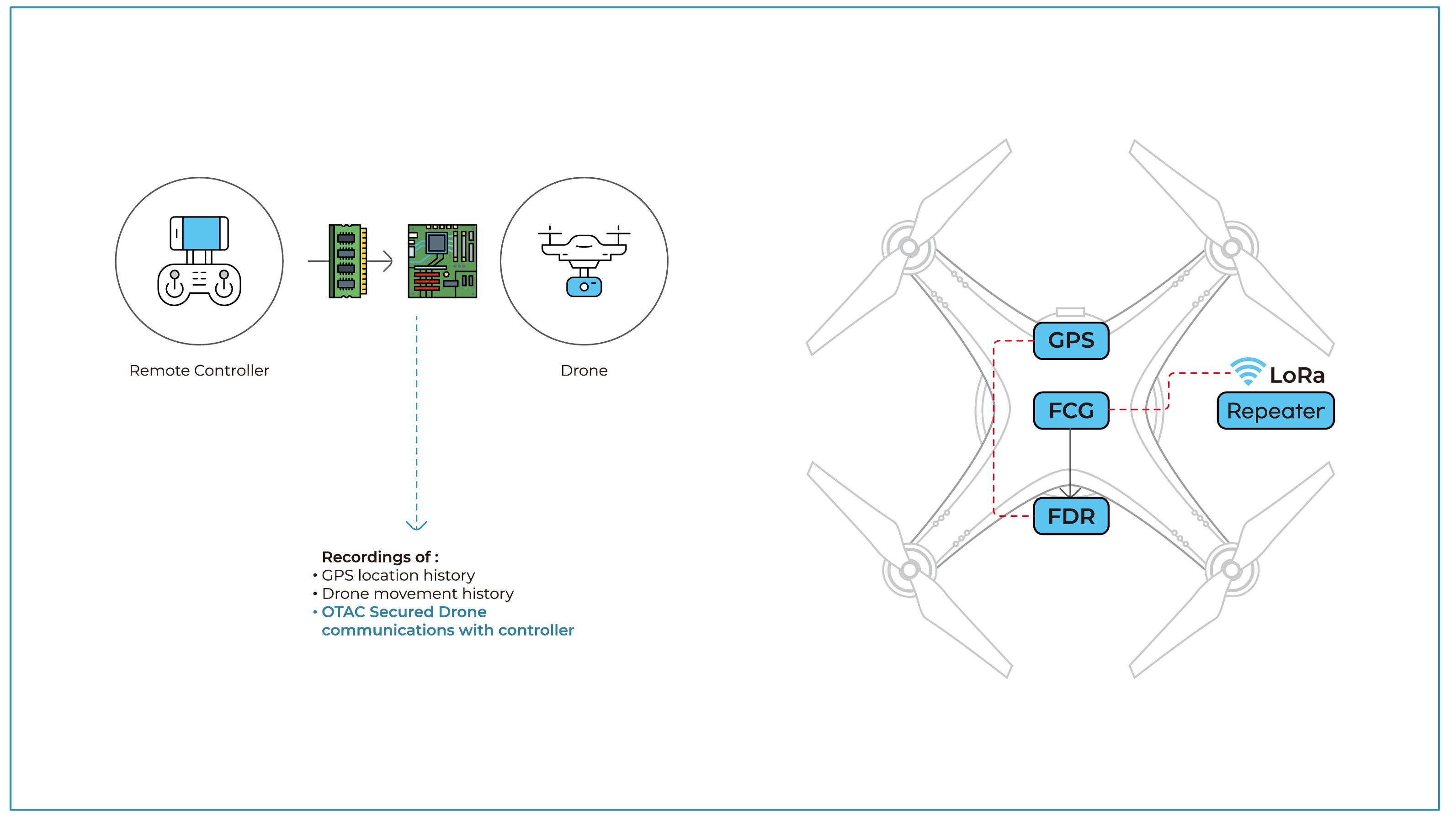
OTAC Drone FDR
FDR (Flight Data Recorder) is a black box for drones; it monitors and tracks any events during the drone flight and missions. The tracking device has a very weak specification on forgery and alteration of data which further leads to being used in wrong deeds. OTAC FDR will be operated at the monitoring and tracking level on the system and will generate dynamic codes to hide the sensitive data for enhancing the information security environment.

The study conducted by the School of Cybersecurity (SCS) at Korea University reveals that the uniqueness of the OTAC code, the predictability of the code, and the security of drones with OTAC are all consistent with theory and practice. You can find more details and download a full report on the website of Hacking and Countermeasure Research Lab (HCRL).
Why OTAC
OTAC, developed by SSenStone, is the original technology that provides all of the following features at the same time.
.svg)
-
OTAC is a dynamic code, which means the code keeps changing. As a result, you don’t need to worry about any leak of your personal information, such as your card details, because the codes must have already been changed when others try to use them.
-
The network connection is NOT necessary at all for generating OTAC.
Reducing an authentication stage that requires the network connection directly means there are fewer gateways for the hackers to access our personal information.
Moreover, this feature enables users to authenticate even when they are in networkless environments, such as on the plane, underground, rural or foreign areas. -
swIDch can guarantee that the code never duplicates with anyone at any given moment.
There is NO chance of someone else having the same code. -
The users or their devices can be identified with the code alone.
Once OTAC has been generated, providing OTAC alone is already fully sufficient to identify the user as the code is unique.
It means, you can forget about the bundles of static information including IDs and passwords.
Insights
Contact Us
make your service reliable with SSenStone!
Inquire now.
5F, 329, Cheonho-daero Dongdaemun-gu, Seoul, Republic of Korea
Contact below if you have an urgent inquiry.
Korea Office (SSenStone)
5F, 329, Cheonho-daero Dongdaemun-gu, Seoul, Republic of Korea (02622)
Tel : 02-569-9668 | Fax : 02-6455-9668
im@ssenstone.com
UK Office (swIDch)
Floor 1, 3 More London SE1 2RE, United Kingdom
Tel : 020-3283-4563
info@swidch.com



