OTAC Solutions
Endpoint OTAC
SSenStone's Endpoint OTAC surpasses the vulnerability of password-based authentication methods, offering a secure and advanced user authentication process using one-way dynamic codes, eliminating the risk of duplication.
Pain points
In the age of industrial automation, the worldwide manufacturing landscape is transitioning towards an integrated operational technology (OT) and information technology (IT), designed to efficiently oversee a multitude of devices and equipment. However, this shift exposes the system to external threats due to the lack of an advanced authentication system tailored to identify users and devices suitable for this evolving environment. The vulnerability of the system became evident during the programmable logic controller (PLC) attack on the Israeli water treatment system, resulting in the paralysis of water treatment processes and water pollution. Similarly, a water treatment facility in Florida experienced a rapid increase in chemical concentrations due to PLC hacking, posing a potential risk of tangible damage. Furthermore, critical infrastructures such as power plants, power grids, manufacturing plants, gas lines, and essential facilities like fleets, fighter jets, and missile manufacturing plants, where PLCs play a pivotal role, have fallen victim to hacking breaches.
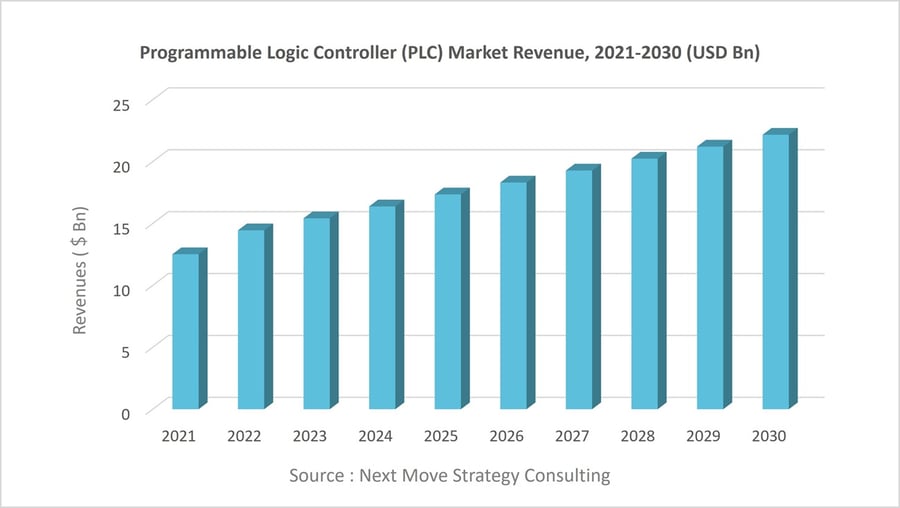
Considering the forecasted surge in global PLC demand to $22.17 billion by 2030 (source: Next Move Strategy Consulting), propelled by the automation of manufacturing facilities and management systems, it becomes imperative to advance user authentication technology. This advancement is crucial to fundamentally obstruct access to OT and PLC equipment by unauthorised users relying on secured passwords, thus mitigating the risks associated with exposure or sharing of such credentials.
- Lack of Endpoint Security Management in OT Environments
-
-
- Endpoints in OT environments encompass a wide range of devices such as PLCs, RTUs, DCS, HMIs, and SCADA systems. While IT infrastructure has adopted advanced security frameworks such as Multi-Factor Authentication (MFA) and Role-Based Access Control (RBAC), many OT endpoints still rely on static, hardcoded passwords. Exploiting this weakness, attackers often target vulnerable endpoints as entry points to easily compromise OT systems.
-
- Constant Exposure to Threats via fixed value-based PLC Login
The use of fixed values such as passwords to access the PLC poses a persistent security risk. A fixed value makes it highly susceptible to security breaches. Beyond the PLC management personnel, individuals with knowledge of the password, including external partners, retirees, and contract workers, can easily gain access to the PLC, exposing it to potential security threats at any given time. Even when operating within a closed network, the risk of potential hacking threats remains ever-present. Moreover, instances of malicious code infecting terminals (such as laptops and HMIs) connected to the PLC and the PLCs themselves are not uncommon when using password recovery tools. Unfortunately, the absence of a suitable alternative leaves the issue unresolved, preventing the implementation of preemptive measures.
- Deployment Limitations Due to Multiple PLC Devices
Unlike being directly chosen by end-users, the selection of most PLC devices is typically made during the delivery of various control devices by system integrators responsible for constructing automated process facilities. Consequently, many end-users find themselves utilising products from multiple manufacturers, each employing different security technologies simultaneously. This reality makes it realistically challenging for end-users to articulate and demand security solutions concerning access authentication for various automation devices, including PLCs.
- Weak Security Management Without PLC Security Experts
Typically, the security department within a company oversees Human-Machine Interface (HMI) systems - terminals, workstations, and etc. - and the network switch situated directly in front of the PLC. PLCs are predominantly categorised as electrical devices and facilities, often falling under the purview of the control & facility department. In essence, as the PLC exists beyond the management scope of the security department, its security is reliant on the proposed security level by the control device or system supplier. Even if an end user wishes to enhance security, the verification of security and stability must be endorsed by the control equipment supplier, potentially leading to maintenance and repair challenges in the future.
- Burden of OT & PLC System Upgrades
Enhancing security for existing OT systems often demands considerable time, workforce, and resources, thereby incurring costs for Industrial Control System (ICS), OT organisations, and manufacturers. This challenge arises from the necessity for PLCs to continue normal operations despite their inherent vulnerabilities. In practical terms, some end users attempted to implement multi-factor authentication (MFA) for their PLCs. However, many abandoned this effort due to the extensive changes required not only in software but also in hardware and infrastructure to incorporate the new authentication technology. The more end users, feeling encumbered by the upgrades, postpone their schedules, the greater the exposure of their PLCs and operating systems to potential risks.
Solutions
SSenStone's Endpoint OTAC addresses these challenges by offering an authentication process tailored for industrial control systems (ICS) and OT environments. Utilising the world's first one-way dynamic authentication (OTAC) technology, it ensures high security with minimal resource requirements. OTAC permits only authorised users and devices to access the PLC, proactively thwarting potential attacks like packet sniffing.

Compliance with OT Cybersecurity Frameworks
SSenStone’s Endpoint OTAC addresses key cybersecurity regulations — including the NIS2 Directive, Cyber Resilience Act (CRA), NERC CIP Standards, and IEC 62443 — through advanced, OT-optimised authentication mechanisms.
■ NIS2 Compliance: Endpoint OTAC enables secure, passwordless access to OT systems, eliminating vulnerabilities associated with static credentials and meeting the security measures required under the NIS2 Directive.
■ CRA Compliance: By replacing traditional password-based systems with dynamic authentication codes, Endpoint OTAC helps reduce the risk of unauthorised access and streamlines the authentication process, aligning with the Cyber Resilience Act.
- ■ NERC CIP Compliance: Endpoint OTAC uses dynamic authentication codes to block unauthorised access at the source, providing secure user authentication. Comprehensive audit trails and access logs support monitoring and control, in line with NERC CIP Standards.
- ■ IEC 62443 Compliance: Through one-time authentication codes (OTAC), SSenStone’s OT authentication solutions meet the ‘Identification & Authentication Control’ requirements of FR1, while also supporting ‘Use Control’ under FR2. This ensures that only authorised users can access the system, with clear audit trails for accountability.
Neutralise Password Vulnerabilities with a Dynamic Authentication Code
SSenStone's OTAC stands as the exclusive technology capable of proactively thwarting security threats associated with device and user authentication, acknowledged as vulnerabilities in both OT and PLC devices. By supplying an authentication value through a dynamic code generated anew with each use, OTAC effectively eliminates prevailing issues linked to password-based authentication, which rely on fixed values. Consequently, this approach neutralises potential hacking threats arising from password cracking software and password sharing among PLC users. Furthermore, the need to assign a password to each individual PLC device is eradicated, simplifying PLC management. This ease extends to granting specific permissions to retirees, contract workers, and others, restricting their access to designated devices or periods.
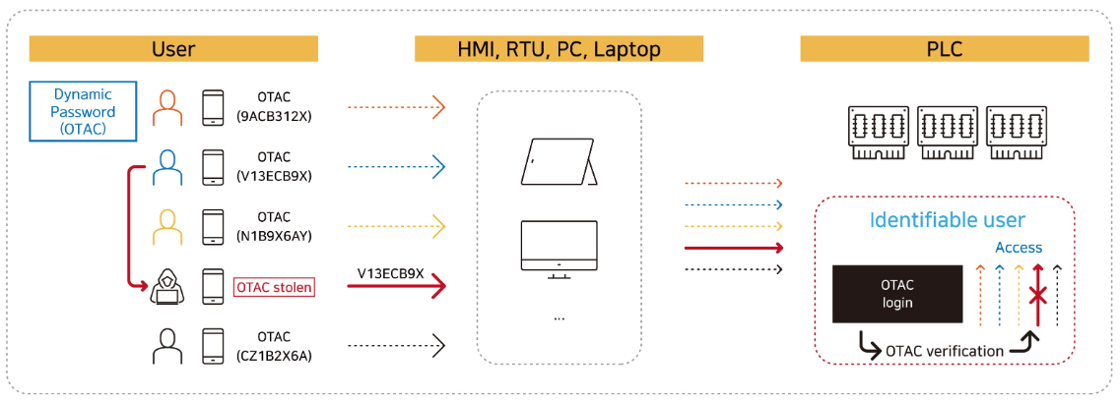
[Issues with current PLC certification using just passwords]
⇛ Password sharing between engineers
⇛ Access is granted to users who are indistinguishable (un-identified)
⇛ If a password is stolen (from any user) it can be later used to gain access without any further challenge
.png?width=2000&height=697&name=img_plcotac_before%20(eng).png)
[Issues resolved by using OTAC-based authentication]
⇛ No password sharing – users enter dynamic codes (OTAC) which are generated differently each time
⇛ Access is only granted to authorised users – who are also fully identifiable
⇛ If the OTAC is stolen and later used it will be denied access by the OTAC verification module
⇛ All of this is possible without any need to modify the existing password interface (8-digit example above)
Tailored Design for an Optimised Authentication for End User
The PL), a fundamental component for integrated operation and control in the OT sector for production automation, has traditionally adhered to varied authentication processes based on the internal infrastructure and operational policies of individual companies. However, SSenStone's Endpoint OTAC is meticulously crafted to align with the preferences of each end user, ensuring effortless deployment. This design flexibility extends to configuring authentication codes, ranging from the commonly used 6 to 9 digits, to those exceeding 9 digits. Additionally, users can select their preferred authentication code issuance medium, be it through a smartphone or a display card.
[Authentication code generation and PLC device management by smartphone]
.jpg?width=1000&height=562&name=img_plcotac_app%20(eng).jpg)
Preserve UX and UI While Introducing Standardisation in the Authentication Process
Leveraging expertise validated through Proof of Concept (PoC) and Minimum Viable Product (MVP) initiatives with prominent global PLC manufacturers, SSenStone incorporates an authentication process that enables end users to uphold the current user experience (UX) and user interface (UI) or make minimal adjustments. Furthermore, by introducing a standardised procedure facilitating straightforward registration and management of devices and users, end users can seamlessly integrate an advanced authentication process.
[Example PoC success case from current client utilising OTAC technology]
.png?width=1000&height=480&name=img_plcotac_process%20(eng).png)
Benefits
SSenStone's Endpoint OTAC aids PLC manufacturers and operators in enhancing security by eradicating vulnerabilities associated with password usage, all achieved with minimal computing resources. Moreover, it contributes to reducing system disruptions, ensuring a seamless application of systems. The heightened productivity and efficiency, crucial elements in industrial control systems (ICS) and OT systems, consequently enhance the competitiveness of organisations, enterprises, and institutions reliant on production and service automation.
Substantial Savings on Manpower and Costs
Endpoint OTAC offers an enhancement to the user authentication process while keeping the existing infrastructure intact, eliminating the need to augment PLC hardware specifications or alter the current network environment. This results in a notable reduction in both the cost and time required for constructing a new authentication process. In fact, considerable cost savings can be anticipated compared to alternative certification solutions.
Enhanced Productivity and Efficiency
Endpoint OTAC features an exceptionally compact algorithm code size, enabling code generators to be implemented in various formats such as smartphones and display cards. Additionally, its minimal central processing unit (CPU) overhead, when contrasted with other authentication and encryption methods, permits application to a central back-end server or the PLC's lightweight module. The system offers adaptable code parameters, allowing integration with minimal UI changes and application to existing infrastructure, thereby eliminating the necessity for extensive, costly infrastructure alterations.
Effortless Management without Technical Hurdles
Access to the PLC is only attainable through an OTAC generated by an authentication code generator, which includes the PLC manager's smartphone. This ensures that PLC and PC devices accessible to each user can be restricted, enhancing management efficiency. Notably, the setup process for device and user authentication is straightforward, enabling management without the requirement for specialised technical skills or training courses.
Why OTAC
OTAC, developed by SSenStone, is the original technology that provides all of the following features at the same time.
-
OTAC is a dynamic code, which means the code keeps changing. As a result, you don’t need to worry about any leak of your personal information, such as your card details, because the codes must have already been changed when others try to use them.
-
The network connection is NOT necessary at all for generating OTAC.
Reducing an authentication stage that requires the network connection directly means there are fewer gateways for the hackers to access our personal information.
Moreover, this feature enables users to authenticate even when they are in networkless environments, such as on the plane, underground, rural or foreign areas. -
swIDch can guarantee that the code never duplicates with anyone at any given moment.
There is NO chance of someone else having the same code. -
The users or their devices can be identified with the code alone.
Once OTAC has been generated, providing OTAC alone is already fully sufficient to identify the user as the code is unique.
It means, you can forget about the bundles of static information including IDs and passwords.
OTAC Algorithm Analysis and Academic Verification

New Excellent Technology (NET) Certification Acquired

SSenStone has received the NET Certification from the Ministry of Trade, Industry, and Energy for its "Individual IoT Device Authentication and Transmission Data Security Technology through Unidirectional Dynamic Authentication (OTAC)."
International Common Criteria (CC) Certification Achieved
.png?width=150&height=150&name=%EA%B5%AD%EC%A0%9CCC%EC%9D%B8%EC%A6%9D_%EC%97%A0%EB%B8%94%EB%9F%BC%20(png).png)
OTACTokenV1.0, the authentication solution based on the world’s first unidirectional dynamic authentication technology, OTAC, has earned the international Common Criteria (CC) certification. For more information, please refer to the press release.
OTAC for Phygital Wins IR52 Jang Yeong-sil Award

SSenStone's OTAC for Phygital has been awarded the 40th-week IR52 Jang Yeong-sil Award for 2024, hosted by the Ministry of Science and ICT. For more details, please visit the official IR52 Jang Yeong-sil Award homepage or the press release.
Insights
Contact Us
make your service reliable with SSenStone!
Inquire now.
5F, 329, Cheonho-daero Dongdaemun-gu, Seoul, Republic of Korea (02622)
Contact below if you have an urgent inquiry.
Korea Office (SSenStone)
5F, 329, Cheonho-daero Dongdaemun-gu, Seoul, Republic of Korea (02622)
Tel : 02-569-9668 | Fax : 02-6455-9668
im@ssenstone.com
UK Office (swIDch)
Floor 1, 3 More London SE1 2RE, United Kingdom
Tel : 020-3283-4563
info@swidch.com


.jpg?width=2000&height=1164&name=img_plcotac_case%20box_ls%20(eng).jpg)
.jpg?width=2000&height=1166&name=img_plcotac_case%20box%20(eng).jpg)



